Originally published by South-End Tech Limited
Written by Patrick Meki, Cybersecurity & IT Risk Analyst at South-End Tech Limited.
The original version can be accessed here
Introduction
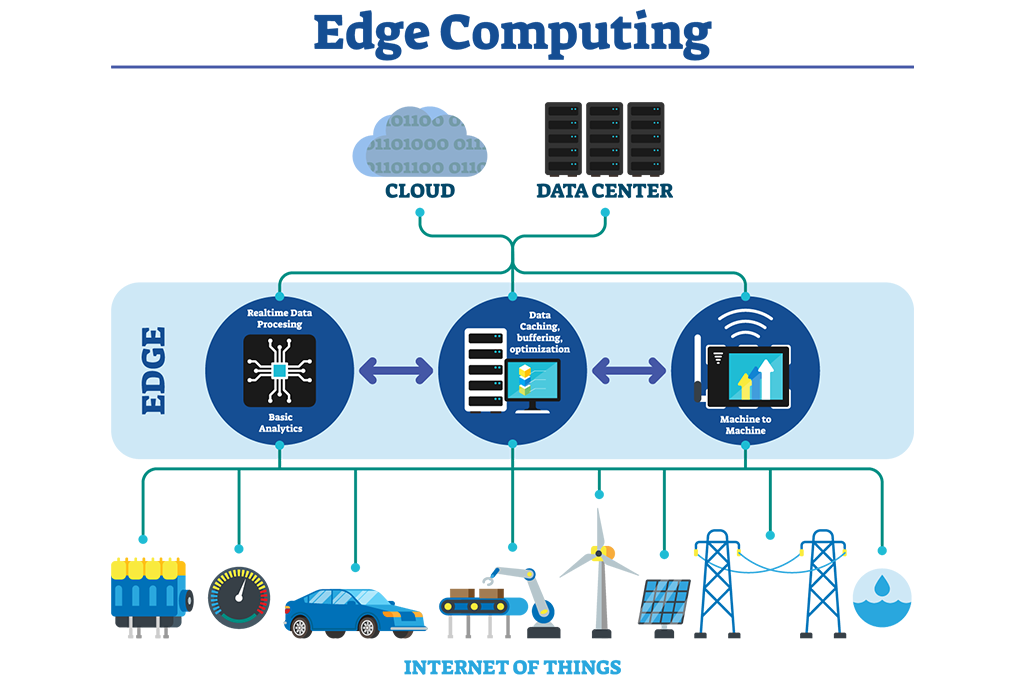
Edge computing is reshaping how organizations process and use data. Instead of relying solely on centralized cloud servers, edge computing pushes processing closer to where data is generated whether on IoT devices, healthcare systems, or in most cases, end-user devices. This approach reduces latency thus improving performance immensely with an additional support of real-time decision-making.
However, while the edge promises efficiency and innovation, it also introduces unique cybersecurity risks. With end-devices spread across diverse environments, attackers now have more opportunities to exploit weak security controls. This loophole calls for a fresh look at cybersecurity strategies on protecting the edge.
Why Edge Matters for Cybersecurity
Unlike traditional centralized IT environments, edge computing environments are:
1. Highly Decentralized
– Data is processed across thousands of nodes thereby making each a potential target.
2. IoT-Driven
– In this era where we have billions of sensors, wearables, and connected devices across the internet, these advances have enabled expansion of the attack surface.
3. Closer to the User
– With data handled locally, risks of data leakage, tampering, or physical compromise has increased.
4. Mission Critical
– Many edge systems power healthcare, transportation, and smart city services, where downtime or compromise can be devastating.
Key Cybersecurity Threats at the Edge
1. Insecure IoT Devices
– Many IoT devices lack strong security features, making them easy targets for malware and botnets.
2. Data Privacy Risks
– Sensitive data, such as health records or financial transactions, processed at the edge could be exposed if encryption is weak or absent.
3. Supply Chain Attacks
– Edge hardware and software often come from multiple vendors, raising the risk of compromised components or hidden backdoor.
4. Physical Tampering
– Edge devices deployed in remote or public locations are vulnerable to theft or manipulation.
5. API and Software Vulnerabilities
– Weak or unmonitored APIs can provide attackers with direct access to critical systems.
Best Practices for Securing Edge Environments
1. Adopt Zero-Trust Principles
– Authenticate every user and device continuously, assuming no node is inherently trusted.
2. Strong Device Authentication
– Apply MFA to every aspect of the edge where applicable.
3. Encrypt Data Everywhere
– Both at rest and in transit, ensuring sensitive data cannot be intercepted.
4. Continuous Monitoring & AI Detection
– Deploy endpoint detection tools that leverage AI to flag anomalies in real time.
5. Patch & Update Regularly
– Maintain a strict patching cycle for IoT and edge devices, which are often left unpatched.
6. Vendor & Supply Chain Vetting
– Work with trusted partners and verify software/hardware integrity before deployment.
Conclusion
Edge computing is the backbone of the next wave of digital transformation. From powering autonomous transport to enabling smart cities, its potential is vast. But the same decentralization that makes it powerful also makes it vulnerable.
Organizations must treat edge security as a priority, not an afterthought. By embedding zero-trust, encryption, and robust monitoring into their edge strategies, businesses can harness the benefits of edge computing without exposing themselves to unnecessary risks.
Comments (0)
No comments yet. Be the first to comment!